A secure image steganography framework for covert communication using asymmetric encryption and Huffman Compression
Keywords:
Asymmetric communication, Covert Communication, Huffman Compression, Information Security, SteganographyAbstract
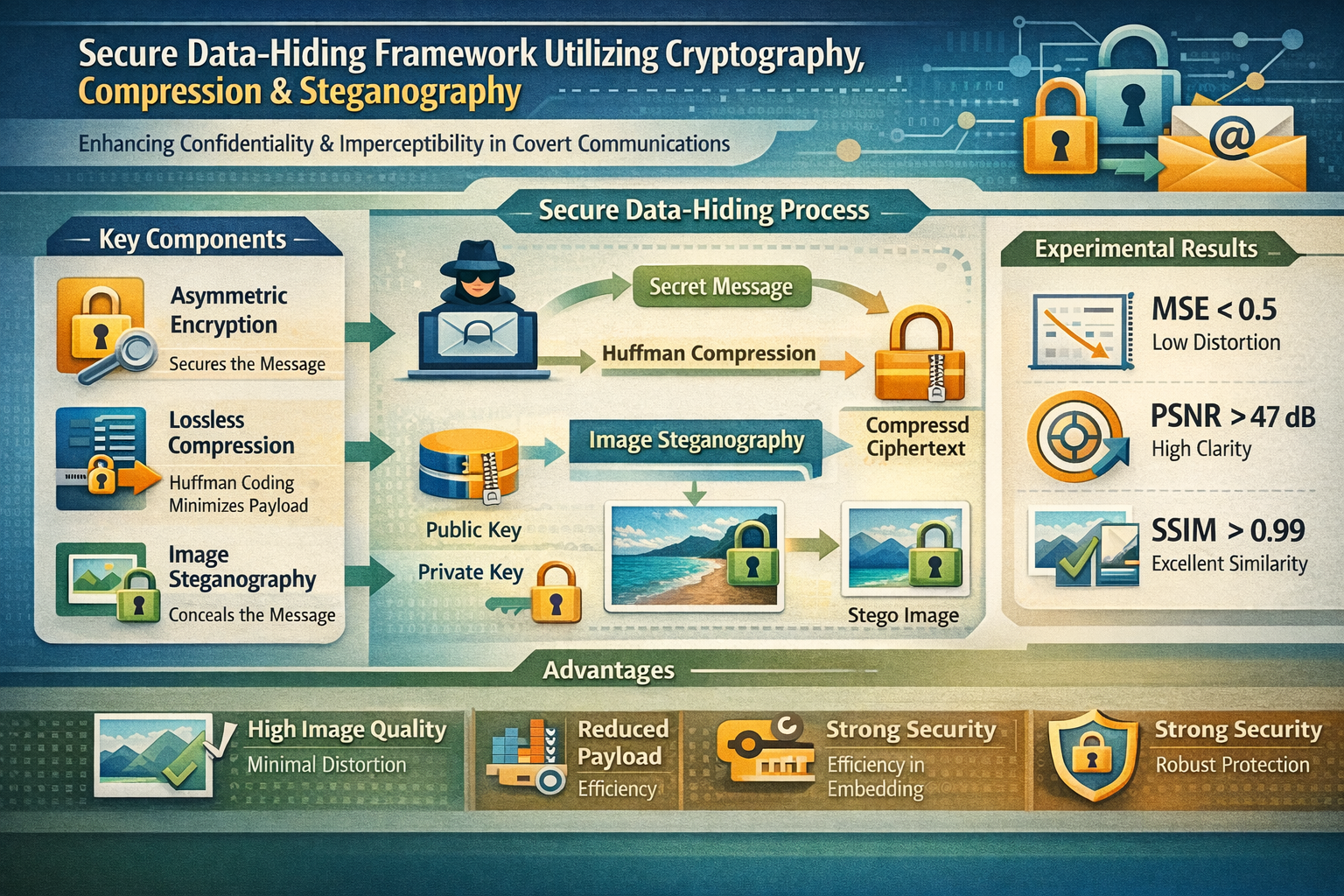
This paper presents a secure data-hiding framework that combines asymmetric key cryptography, lossless data compression, and image steganography to enhance the confidentiality and imperceptibility of hidden communications. The proposed method encrypts the secret message using an asymmetric encryption scheme, compresses the resulting ciphertext using Huffman coding, and embeds the compressed data into a digital image using a spatial-domain steganographic technique. This multi-layered approach ensures that both the existence and the content of the secret message are protected. Experimental evaluations were conducted using standard image quality metrics, including Mean Squared Error (MSE), Peak Signal-to-Noise Ratio (PSNR), and Structural Similarity Index Measure (SSIM), to assess visual imperceptibility, along with performance analysis to evaluate computational overhead. The results demonstrate that the proposed method achieves high image quality with minimal distortion while maintaining strong cryptographic security. The integration of compression effectively reduces embedding payload, further improving steganographic performance. The findings indicate that the proposed framework provides a robust and practical solution for secure and covert data transmission.
References
Ahmed, M., & Abed, F. (2022). A hybrid cryptography–steganography approach for secure data communication. Journal of Information Security and Applications, 66, 103161.
Ahmed, N., & Abdullah, M. (2021). Improving image steganography using compression and encryption techniques. Journal of Information Security and Applications, 61, 102933.
alfo1995. (2026). Huffman-Algorithm.
Alkhliwi, S. (2023). Huffman encoding with white tailed eagle algorithm-based image steganography technique. Engineering, Technology & Applied Science Research, 13(2), 10453–10459.
Almazaydeh, W. I. A., Sheshadri, H. S., & Padma, S. K. (2018). A novel approach of image steganography for secret communication using spacing method. International Journal of Computer Networks & Communications (IJCNC).
Anderson, R., Barton, C., Böhme, R., Clayton, R., van Eeten, M., Levi, M., Moore, T., & Savage, S. (2020). Measuring the cost of cybercrime. Journal of Cybersecurity, 6(1), 1–19.
Ashari, I. F. (2022). The evaluation of audio steganography to embed image files using encryption and Snappy compression. The Indonesian Journal of Computer Science, 11(2), 3050.
Bernstein, D. J., & Bhargavan, K. (2020). The security impact of RSA padding schemes. IEEE Security & Privacy, 18(3), 38–45.
Cheddad, A., Condell, J., Curran, K., & McKevitt, P. (2020). Digital image steganography: Survey and analysis of current methods. Signal Processing, 176, 107676.
Elshamy, [Authors as per article]. (2024). Image Steganography: A Comparative and Practical Study. International Journal of Intelligent Computing and Information Sciences, 24(2), 41–57. https://doi.org/10.21608/ijicis.2024.290869.1337
Gonzalez, R. C., & Woods, R. E. (2002). Digital image processing. Proceedings of the IEEE, 90(4), 716–720.
Huffman, D. A. (1952). A method for the construction of minimum-redundancy codes. Proceedings of the IRE, 40(9), 1098–1101.
Huynh-Thu, Q., & Ghanbari, M. (2008). Scope of validity of PSNR in image/video quality assessment. Electronics Letters, 44(13), 800–801.
Kahn, A., & Khan, M. A. (2021). Public key cryptography: State of the art and future challenges. Journal of Information Security and Applications, 58, 102712.
Kadhem, E. L., & Baawi, S. S. (2023). A secure and high capacity image steganography approach using Huffman coding and RSA encryption. Journal of Al-Qadisiyah for Computer Science and Mathematics, 15(2), 35–50.
Li, X., Wang, J., & Yang, Y. (2021). Secure image steganography based on adaptive embedding strategies. Journal of Visual Communication and Image Representation, 74, 102983.
Morkel, T., Eloff, J., & Olivier, M. (2005). An overview of image steganography. Information and Computer Security, 13(4), 319–331.
Nguyen, D., T. (2025). A secure image steganography based on Hamming codes and image block complexity estimation using a zig-zag order. Journal of Science and Technology on Information Security, 2(25), 21–42.
Rahman, S., Uddin, J., Hussain, H., Ahmed, A., Khan, A. A., Zakarya, M., Rahman, A., & Haleem, M. (2023). A Huffman code LSB based image steganography technique using multi-level encryption and achromatic component of an image. Scientific Reports, 13, 14183. https://doi.org/10.1038/s41598-023-41303-1
Ramadhan, I. F., De La Croix, N. J., Ahmad, T., & Uzamurengera, A. (2025). Huffman coding-based data reduction and quadristego logic for secure image steganography. Engineering Science and Technology, an International Journal, 65, 102033.
Ramadhan, I. F., De La Croix, N. J., Ahmad, T., & Uzamurengera, A. (2025). IRJT-Secure: Open-source image steganography with Quadristego embedding and Huffman compression. Software Impacts, 26, 100801.
Singh, R., & Verma, A. (2023). Enhancing multimedia security using asymmetric encryption and image steganography. Multimedia Tools and Applications, 82(7), 10423–10445.
Stallings, W. (2019). Cryptography and network security: principles and practice. IEEE Security & Privacy, 17(2), 88–91.
Susanto, A., Sinaga, D., & Mulyono, I. U. W. (2024). PSNR and SSIM Performance Analysis of Schur Decomposition for Imperceptible Steganography. Scientific Journal of Informatics, 11(3), 803–810. https://doi.org/10.15294/sji.v11i3.9561
Wang, Z., Bovik, A. C., Sheikh, H. R., & Simoncelli, E. P. (2004). Image quality assessment: From error visibility to structural similarity. IEEE Transactions on Image Processing, 13(4), 600–612.
Wijayanto, E. F., Zarlis, M., & Situmorang, Z. (2018). Increase the PSNR of image using LZW and AES algorithm with MLSB on steganography. International Journal of Engineering and Technology, 7(2.5), 119–121.