Recurrent neural network for adaptive cyber attack prediction on critical defense systems
Keywords:
Adaptive Intrusion Detection, Critical Defense System, Cyber Attack Prediction, RNNAbstract
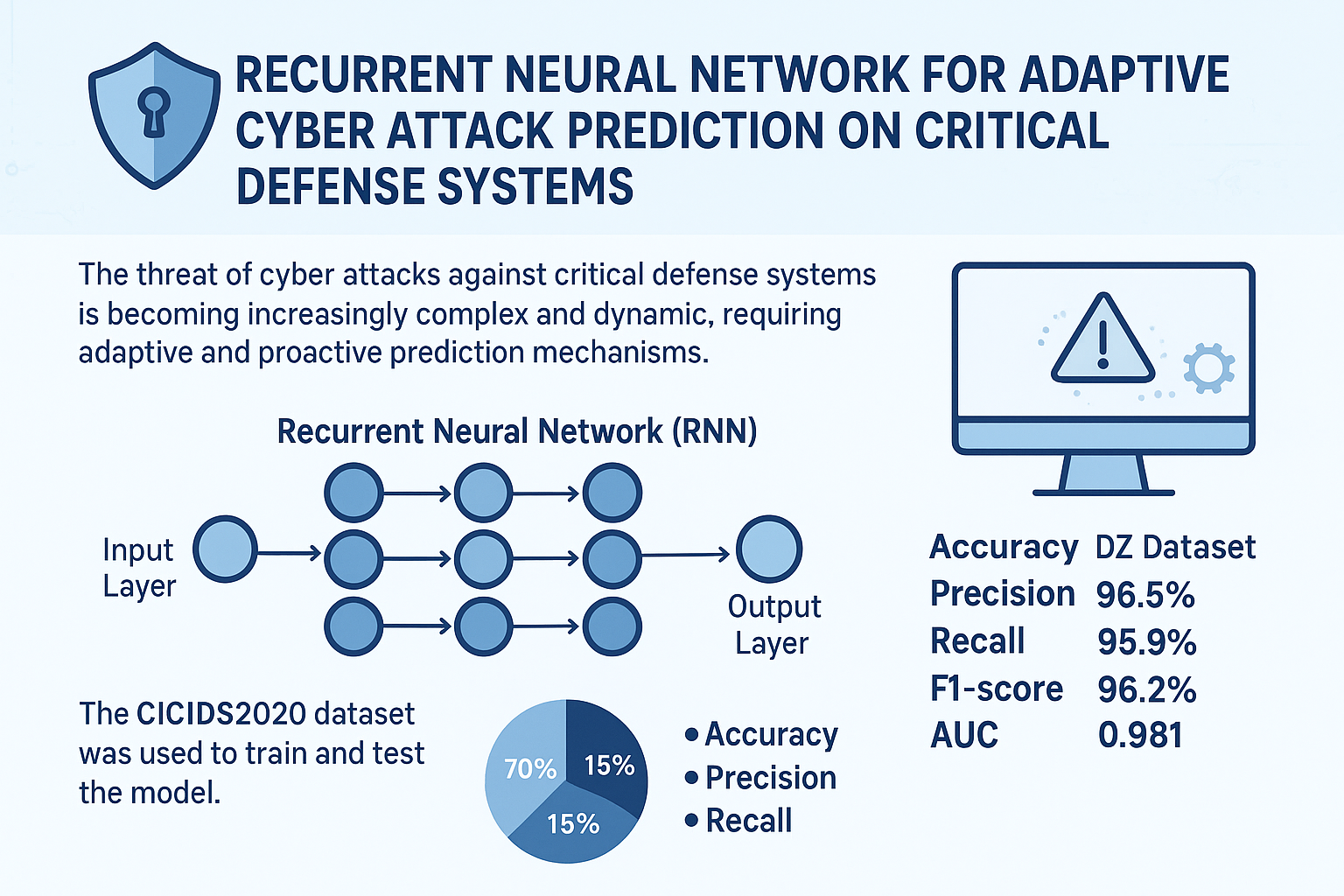
The threat of cyber attacks against critical defense systems is becoming increasingly complex and dynamic, requiring adaptive and proactive prediction mechanisms. This study aims to develop a Recurrent Neural Network (RNN) model to predict cyber attacks on critical defense systems with high accuracy and generalization capabilities against new attacks. The CICIDS2020 dataset was used to train and test the model, with 70% of the data allocated for training, 15% for validation, and 15% for testing. The RNN architecture was optimized by selecting the number of hidden layers, the number of neurons per layer, the activation function, and the application of dropout and regularization to minimize the risk of overfitting. The model was trained using the Backpropagation Through Time (BPTT) algorithm and evaluated using accuracy, precision, recall, F1-score, and AUC metrics. The results show that RNN outperforms LSTM, Random Forest, and SVM algorithms, with an accuracy of 97.8%, precision of 96.5%, recall of 95.9%, F1-score of 96.2%, and AUC of 0.981, and is capable of detecting rare attacks. These findings confirm the effectiveness of RNN in capturing long-term temporal patterns in cyberattack data and providing adaptive predictions for new attacks. The practical implications of this research include strengthening critical defense systems through early detection and real-time mitigation of cyberattacks, as well as providing a basis for the development of reliable proactive security systems.
References
Adeyeri, A., & Abroshan, H. (2024). Geopolitical Ramifications of Cybersecurity Threats: State Responses and International Cooperations in the Digital Warfare Era. Information (Switzerland), 15(11), 682. https://doi.org/10.3390/info15110682
Alijoyo, F. A., Kaur, C., Anjum, A., Vuyyuru, V. A., & Bala, B. K. (2024). Enhancing Cyber-Physical Systems Resilience: Adaptive Self-Healing Security Using Long Short-Term Memory Networks. Proceedings - 3rd International Conference on Advances in Computing, Communication and Applied Informatics, ACCAI 2024, 1–8. https://doi.org/10.1109/ACCAI61061.2024.10602467
Anwar, S., Zain, J. M., Zolkipli, M. F., Inayat, Z., Khan, S., Anthony, B., & Chang, V. (2017). From intrusion detection to an intrusion response system: Fundamentals, requirements, and future directions. Algorithms, 10(2), 39. https://doi.org/10.3390/a10020039
Bilan, Y., Oliinyk, O., Mishchuk, H., & Skare, M. (2023). Impact of information and communications technology on the development and use of knowledge. Technological Forecasting and Social Change, 191, 122519. https://doi.org/10.1016/j.techfore.2023.122519
Burmaoglu, S., Saritas, O., & Yalcin, H. (2019). Defense 4.0: Internet of Things in Military. In Emerging Technologies for Economic Development (pp. 303–320). Springer. https://doi.org/10.1007/978-3-030-04370-4_14
Dari, S. S., Thool, K. U., Deshpande, Y. D., Aush, M. G., Patil, V. D., & Bendale, S. P. (2023). Neural Networks and Cyber Resilience: Deep Insights into AI Architectures for Robust Security Framework. Journal of Electrical Systems, 19(3), 78–95. https://doi.org/10.52783/jes.653
Díaz-Verdejo, J., Muñoz-Calle, J., Alonso, A. E., Alonso, R. E., & Madinabeitia, G. (2022). On the Detection Capabilities of Signature-Based Intrusion Detection Systems in the Context of Web Attacks. Applied Sciences (Switzerland), 12(2), 852. https://doi.org/10.3390/app12020852
Dr. Zeeshan Faisal Khan. (2025). Cyber Warfare and International Security: A New Geopolitical Frontier. The Critical Review of Social Sciences Studies, 3(2), 513–527. https://doi.org/10.59075/k9cbhz04
Ghanem, K., Aparicio-Navarro, F. J., Kyriakopoulos, K. G., Lambotharan, S., & Chambers, J. A. (2017). Support Vector Machine for Network Intrusion and Cyber-Attack Detection. 2017 Sensor Signal Processing for Defence Conference, SSPD 2017, 2017-January, 1–5. https://doi.org/10.1109/SSPD.2017.8233268
Guerra, G. A. L. R. (2024). Contested Logistics as an evolution of military logistics using technological tools. J. Comput. Electron. Sci.: Theory Appl., 5, 5–27. https://doi.org/10.17981/cesta.05.02.2024.01
Gupta, R., Srivastava, D., Sahu, M., Tiwari, S., Ambasta, R. K., & Kumar, P. (2021). Artificial intelligence to deep learning: machine intelligence approach for drug discovery. Molecular Diversity, 25(3), 1315–1360. https://doi.org/10.1007/s11030-021-10217-3
Islam, M. T. (2025). Adversarial Defence Mechanisms in Neural Networks for Ics Fault Tolerance: a Comparative Analysis. ASRC Procedia: Global Perspectives in Science and Scholarship, 01(01), 404–431. https://doi.org/10.63125/xrp7be57
Khekare, G., Kumar, K. P., Prasanthi, K. N., Godla, S. R., Rachapudi, V., Ansari, M. S. Al, & El-Ebiary, Y. A. B. (2023). Optimizing Network Security and Performance Through the Integration of Hybrid GAN-RNN Models in SDN-based Access Control and Traffic Engineering. International Journal of Advanced Computer Science and Applications, 14(12), 596–606. https://doi.org/10.14569/IJACSA.2023.0141262
Lehto, M. (2022). Cyber-Attacks Against Critical Infrastructure. In Computational Methods in Applied Sciences (Vol. 56, pp. 3–42). Springer. https://doi.org/10.1007/978-3-030-91293-2_1
Li, Y., & Liu, Q. (2021). A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments. Energy Reports, 7, 8176–8186. https://doi.org/10.1016/j.egyr.2021.08.126
Mustafovski, R. (2025). The Use of Communication Platforms in Military Operations: Enhancing Strategic and Tactical Effectiveness. Database Systems Journal, 16.
Padmavathy, R. (n.d.). RNN-Based AI, Cloud Security, and Network Security in Banking: Strengthening Defence and Data Protection.
Pătraşcu, P. (2021). Emerging Technologies and National Security: The Impact of IoT in Critical Infrastructures Protection and Defence Sector. Land Forces Academy Review, 26(4), 423–429. https://doi.org/10.2478/raft-2021-0055
Rani, P., Kotwal, S., Manhas, J., Sharma, V., & Sharma, S. (2022). Machine Learning and Deep Learning Based Computational Approaches in Automatic Microorganisms Image Recognition: Methodologies, Challenges, and Developments. Archives of Computational Methods in Engineering, 29(3), 1801–1837. https://doi.org/10.1007/s11831-021-09639-x
Raparthi, M., Soni, M., Tiwari, V., Dhumane, A., & Sharma, R. (2024). Scalable Implementation of Random Forests for Big Data Classification on Cloud Infrastructure. International Conference on Deep Learning and Visual Artificial Intelligence, 493–512. https://doi.org/10.1007/978-981-97-4533-3_38
Rosenberg, I., Shabtai, A., Elovici, Y., & Rokach, L. (2019). Defense methods against adversarial examples for recurrent neural networks. ArXiv Preprint ArXiv:1901.09963.
Sahin, C. B. (2021). DCW-RNN: Improving class level metrics for software vulnerability detection using artificial immune system with clock-work recurrent neural network. 2021 International Conference on INnovations in Intelligent SysTems and Applications, INISTA 2021 - Proceedings, 1–8. https://doi.org/10.1109/INISTA52262.2021.9548609
Shafi, K., Abbass, H. A., & Zhu, W. (2006). An Adaptive Rule-based Intrusion Detection Architecture. In the Security Technology Conference, The 5th Homeland Security Summit, Australia, 345–355.
Sharma, B. P. (2024). Machine Learning-Driven Approaches for Contemporary Cybersecurity: From Intrusion Detection and Malware Classification to Intelligent Incident Response. Nuvern Machine Learning Reviews, 1(1), 22–32. https://nuvern.com/index.php/nmlr/article/view/3
Sinha, P., Sahu, D., Prakash, S., Yang, T., Rathore, R. S., & Pandey, V. K. (2025). A high performance hybrid LSTM CNN secure architecture for IoT environments using deep learning. Scientific Reports, 15(1), 9684. https://doi.org/10.1038/s41598-025-94500-5
Soe, Y. N., Feng, Y., Santosa, P. I., Hartanto, R., & Sakurai, K. (2019). Rule Generation for Signature Based Detection Systems of Cyber Attacks in IoT Environments. Bulletin of Networking, Computing, Systems, and Software, 8(2), 93–97. http://www.bncss.org/index.php/bncss/article/view/113
Steingartner, W., Galinec, D., & Kozina, A. (2021). Threat defense: Cyber deception approach and education for resilience in hybrid threats model. Symmetry, 13(4), 597. https://doi.org/10.3390/sym13040597
Usman, M. (2024). Securing the Future: The Role of Neural Networks and AI in Advanced Cyber Defense Mechanisms.
Vaseashta, A. (2022). Nexus of Advanced Technology Platforms for Strengthening Cyber-Defense Capabilities. Practical Applications of Advanced Technologies for Enhancing Security and Defense Capabilities: Perspectives and Challenges for the Western Balkans, 14–31. https://doi.org/10.3233/nhsdp220003
Vinayakumar, R., Alazab, M., Soman, K. P., Poornachandran, P., Al-Nemrat, A., & Venkatraman, S. (2019). Deep Learning Approach for Intelligent Intrusion Detection System. IEEE Access, 7, 41525–41550. https://doi.org/10.1109/ACCESS.2019.2895334
Wei, Y., Jang-Jaccard, J., Sabrina, F., Xu, W., Camtepe, S., & Dunmore, A. (2023). Reconstruction-based LSTM-Autoencoder for Anomaly-based DDoS Attack Detection over Multivariate Time-Series Data. ArXiv Preprint ArXiv:2305.09475. http://arxiv.org/abs/2305.09475