Particle Swarm Optimization for Multi Objective Optimization of Intrusion Detection in National Defense Cyber Infrastructure
Keywords:
Cybersecurity, Intrusion Detection System, Multi objective Optimization, Particle Swarm OptimizationAbstract
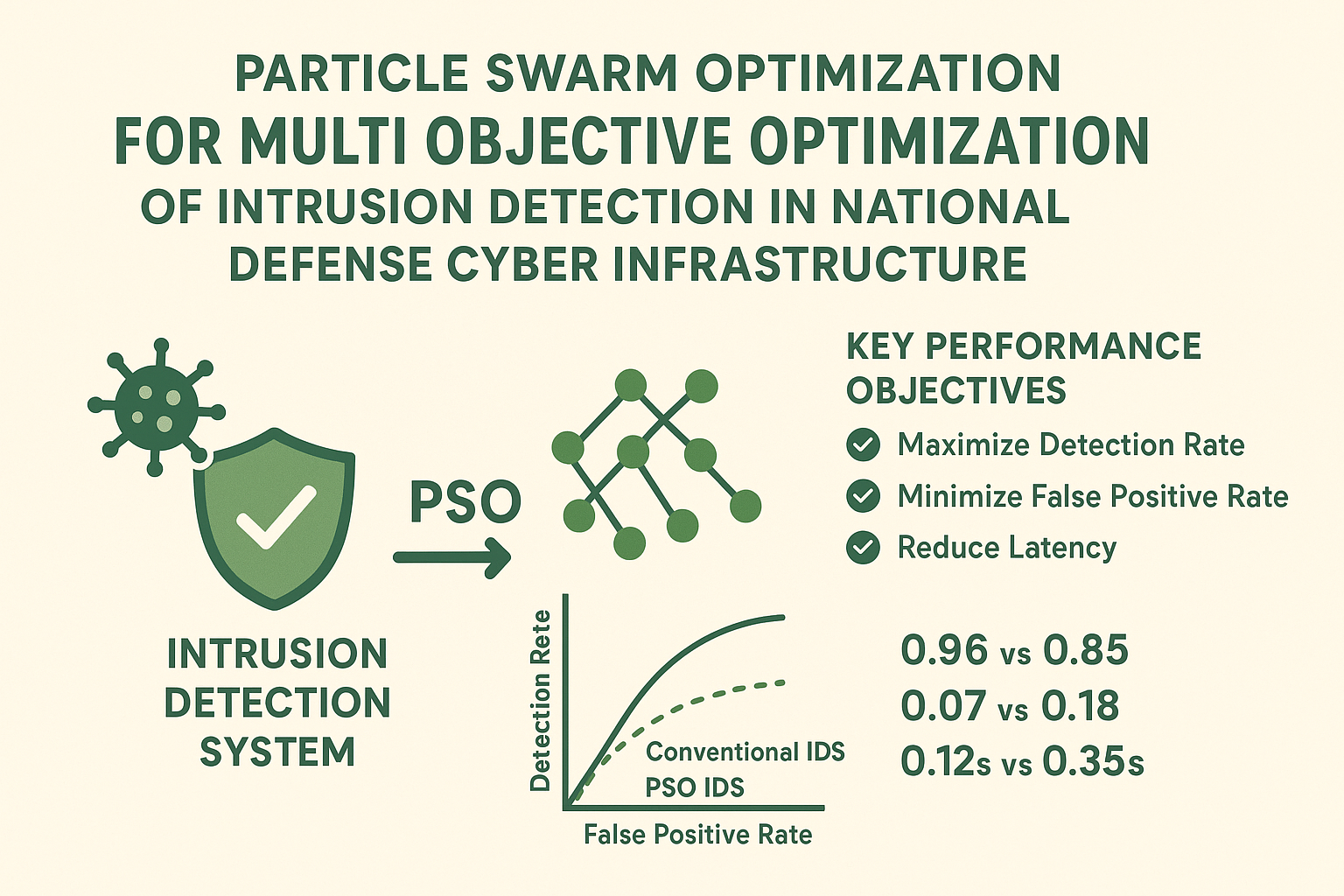
Cybersecurity is a critical component of national defense, yet conventional Intrusion Detection Systems (IDS) often face limitations such as high false positive rates, detection delays, and difficulty adapting to dynamic attack patterns, leading to potential blind spots in defense networks. This study aims to design an adaptive IDS that balances detection accuracy, false positives, and operational efficiency through the application of multi objective Particle Swarm Optimization (PSO). Using the CICIDS2017 dataset, which simulates realistic modern network traffic and attack scenarios, we developed and evaluated a PSO optimized IDS model. The experimental methodology included preprocessing, feature selection, model training, and optimization of key performance objectives—maximizing detection rate (DR), minimizing false positive rate (FPR), and reducing latency. The results demonstrate that the proposed PSO IDS achieved a detection rate of 0.96 compared to 0.85 in conventional IDS, reduced the false positive rate from 0.18 to 0.07, and lowered average detection latency from 0.35 seconds to 0.12 seconds. Pareto front analysis confirmed that the multi objective optimization effectively balances conflicting parameters, delivering more robust and resilient intrusion detection. These findings indicate that PSO based multi objective IDS can serve as a practical and scalable solution for strengthening national cyber defense infrastructures, while also providing policy relevant insights on the integration of AI driven optimization methods into defense strategies.
References
Abdulganiyu, O. H., Tchakoucht, T. A., & Saheed, Y. K. (2024). Towards an efficient model for network intrusion detection system (IDS): systematic literature review. Wireless Networks, 30(1), 453–482. https://doi.org/10.1007/s11276-023-03495-2
Ahmad, Z., Shahid Khan, A., Wai Shiang, C., Abdullah, J., & Ahmad, F. (2021). Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Transactions on Emerging Telecommunications Technologies, 32(1), 1–29. https://doi.org/10.1002/ett.4150
Alazab, M., Awajan, A., Alazzam, H., Wedyan, M., Alshawi, B., & Alturki, R. (2024). A Novel IDS with a Dynamic Access Control Algorithm to Detect and Defend Intrusion at IoT Nodes. Sensors, 24(7), 2188. https://doi.org/10.3390/s24072188
Chen, Y.-F., Lin, F. Y.-S., Tai, K.-Y., Hsiao, C.-H., Wang, W.-H., Tsai, M.-C., & Sun, T.-L. (2025). A near-optimal resource allocation strategy for minimizing the worse-case impact of malicious attacks on cloud networks. Journal of Cloud Computing, 14(1), 41. https://journalofcloudcomputing.springeropen.com/articles/10.1186/s13677-025-00749-6
Chicco, D., Oneto, L., & Tavazzi, E. (2022). Eleven quick tips for data cleaning and feature engineering. PLoS Computational Biology, 18(12), e1010718. https://doi.org/10.1371/journal.pcbi.1010718
Colajanni, M., & Marchetti, M. (2021). Cyber attacks and defenses: Current capabilities and future trends. In Technology and International Relations: The New Frontier in Global Power (pp. 132–151). Edward Elgar Publishing. https://doi.org/10.4337/9781788976077.00015
Dan, V., & Pandey, M. (2024). yber-Security Threats In International Relation The Implications Of Cyber Threats On State Sovereignty, National Security, And International Cooperation, Focusing On Recent Cyber Incidents Rational Analysis In Geographical Point Of View. International Journal of Creative Research Thoughts, 12, 2320–2882. www.ijcrt.org
Dhawas, P., Dhore, A., Bhagat, D., Pawar, R. D., Kukade, A., & Kalbande, K. (2024). Big data preprocessing, techniques, integration, transformation, normalisation, cleaning, discretization, and binning. In Big Data Analytics Techniques for Market Intelligence (pp. 159–182). IGI Global Scientific Publishing. https://doi.org/10.4018/979-8-3693-0413-6.ch006
Gorriz, J. M., Clemente, R. M., Segovia, F., Ramirez, J., Ortiz, A., & Suckling, J. (2024). Is K-fold cross validation the best model selection method for Machine Learning? ArXiv Preprint ArXiv:2401.16407. http://arxiv.org/abs/2401.16407
Harrison, K. R., Elsayed, S., Garanovich, I., Weir, T., Galister, M., Boswell, S., Taylor, R., & Sarker, R. (2020). Portfolio Optimization for Defence Applications. IEEE Access, 8, 60152–60178. https://doi.org/10.1109/ACCESS.2020.2983141
Jain, M., Saihjpal, V., Singh, N., & Singh, S. B. (2022). An Overview of Variants and Advancements of PSO Algorithm. Applied Sciences (Switzerland), 12(17), 8392. https://doi.org/10.3390/app12178392
Kurniabudi, Stiawan, D., Darmawijoyo, Bin Idris, M. Y. Bin, Bamhdi, A. M., & Budiarto, R. (2020). CICIDS-2017 Dataset Feature Analysis with Information Gain for Anomaly Detection. IEEE Access, 8, 132911–132921. https://doi.org/10.1109/ACCESS.2020.3009843
Lansky, J., Ali, S., Mohammadi, M., Majeed, M. K., Karim, S. H. T., Rashidi, S., Hosseinzadeh, M., & Rahmani, A. M. (2021). Deep Learning-Based Intrusion Detection Systems: A Systematic Review. IEEE Access, 9, 101574–101599. https://doi.org/10.1109/ACCESS.2021.3097247
Lin, X., Yang, Z., Zhang, X., & Zhang, Q. (2022). Pareto Set Learning for Expensive Multi-Objective Optimization. Advances in Neural Information Processing Systems, 35, 19231–19247.
Möller, D. P. F. (2023). Cybersecurity in Digital Transformation. In Advances in Information Security (Vol. 103, pp. 1–70). Springer. https://doi.org/10.1007/978-3-031-26845-8_1
Oksuz, K., Cam, B. C., Kalkan, S., & Akbas, E. (2021). Imbalance Problems in Object Detection: A Review. IEEE Transactions on Pattern Analysis and Machine Intelligence, 43(10), 3388–3415. https://doi.org/10.1109/TPAMI.2020.2981890
Roy, A., So, G., & Ma, Y.-A. (2023). Optimization on Pareto sets: On a theory of multi-objective optimization. ArXiv Preprint ArXiv:2308.02145. http://arxiv.org/abs/2308.02145
Saranya, T., Sridevi, S., Deisy, C., Chung, T. D., & Khan, M. K. A. A. (2020). Performance Analysis of Machine Learning Algorithms in Intrusion Detection System: A Review. Procedia Computer Science, 171(2019), 1251–1260. https://doi.org/10.1016/j.procs.2020.04.133
Shami, T. M., El-Saleh, A. A., Alswaitti, M., Al-Tashi, Q., Summakieh, M. A., & Mirjalili, S. (2022). Particle Swarm Optimization: A Comprehensive Survey. IEEE Access, 10, 10031–10061. https://doi.org/10.1109/ACCESS.2022.3142859
Sharafaldin, I., Lashkari, A. H., & Ghorbani, A. A. (2018). Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSP 2018 - Proceedings of the 4th International Conference on Information Systems Security and Privacy, 2018-January, 108–116. https://doi.org/10.5220/0006639801080116
Stewart, H. (2023). Digital Transformation Security Challenges. Journal of Computer Information Systems, 63(4), 919–936. https://doi.org/10.1080/08874417.2022.2115953
Trivedi, V., Varshney, P., & Ramteke, M. (2020). A simplified multi-objective particle swarm optimization algorithm. Swarm Intelligence, 14(2), 83–116. https://doi.org/10.1007/s11721-019-00170-1
Yates, L. A., Aandahl, Z., Richards, S. A., & Brook, B. W. (2023). Cross validation for model selection: A review with examples from ecology. Ecological Monographs, 93(1), e1557. https://doi.org/10.1002/ecm.1557
Yong, Z., Li-juan, Y., Qian, Z., & Xiao-yan, S. (2020). Multi-objective optimization of building energy performance using a particle swarm optimizer with less control parameters. Journal of Building Engineering, 32, 101505. https://doi.org/10.1016/j.jobe.2020.101505
Zhou, C., Hu, B., Shi, Y., Tian, Y. C., Li, X., & Zhao, Y. (2021). A Unified Architectural Approach for Cyberattack-Resilient Industrial Control Systems. Proceedings of the IEEE, 109(4), 517–541. https://doi.org/10.1109/JPROC.2020.3034595